New Notation: Attack-Defence Trees (ADTrees) now available on Vithanco website
Ready to try on the website
What are ADTrees?
Attack-Defence Trees (ADTrees) model security scenarios as a two-player game: an attacker trying to compromise a system and a defender trying to protect it, with their strategies and countermeasures interacting at every level of the tree.
Use ADTrees when you need to model the back-and-forth between attacker and defender. That’s their defining advantage over plain attack trees or risk matrices.
Specifically, ADTrees shine when:
You’re assessing security of a system and want to evaluate defences alongside threats. Rather than listing attacks in one document and defences in another, ADTrees show the countermeasure relationship directly — “this defence counters that attack, but this attack can circumvent that defence.”
You need to communicate security trade-offs to stakeholders. The visual red/green attack/defence distinction makes it immediately readable for non-technical audiences. A CTO can look at an ADTree and see where defences are thin.
You’re doing threat modelling during design. Before building a system, you can map out anticipated attacks, plan defences, and then stress-test those defences by asking “how could an attacker get around this?” — the tree naturally supports this recursive thinking.
Your security scenario has depth. ADTrees handle arbitrary nesting: an attack can be countered by a defence, which can be circumvented by another attack, which can be countered by yet another defence. If your scenario has this layered quality, ADTrees capture it naturally.
When NOT to use them:
If you only care about attacks (no defences), a plain attack tree suffices
If you’re doing root cause analysis of operational problems, use a CRT instead
If you need to model temporal sequences (attack step 1, then step 2), ADTrees are not ideal — they model goal decomposition, not workflows
How do you model ADTrees?
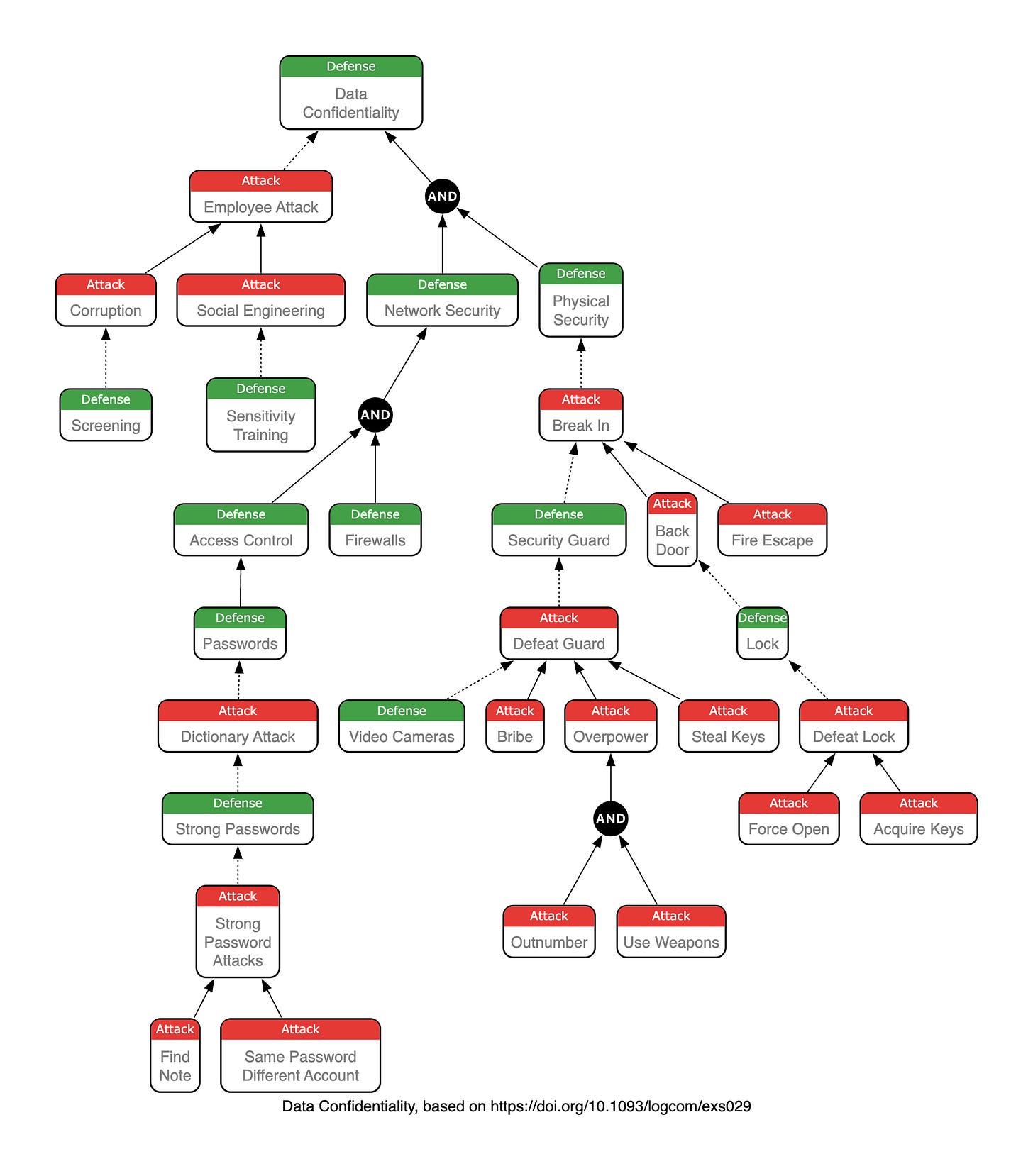
ADTrees extend the classic attack tree formalism by introducing defence nodes alongside attack nodes, allowing you to model the ongoing interaction between attacker and defender in a single diagram. Instead of analysing threats in isolation, you can now visualise how defences counter attacks, how attackers might circumvent those defences, and how the arms race unfolds at every level.
Key features of the ADTree notation:
Two core node types — Attack (red) and Defence (green) — making the diagram immediately readable
Refinement — Break goals into sub-goals, either disjunctively (OR) or conjunctively (AND)
Countermeasures — Connect defences directly to the attacks they counter, and vice versa, to any depth
Flexible root — Start from the defender’s perspective (root = defence) or the attacker’s perspective (root = attack)
The notation is based on the formalism by Kordy, Mauw, Radomirović & Schweitzer published in the Journal of Logic and Computation (DOI: 10.1093/logcom/exs029).
Explore the full notation documentation, including an interactive editor and a worked example modelling data confidentiality in a hosting centre, at: vithanco.com/notations/attack-defense-tree.